SSL certificate replacement of vCenter Server 5.1 & components.
General Info:
SSL files which will be used in the process:
There are seven separate components in vCenter Server 5.1 that utilize certificates to encrypt communication
Here is what we are gonna do:
Download the SSL Automation tool
Version 1.0 of the tool is supported with vSphere 5.1
Version 1.0.1 of the tool is supported with vSphere 5.1 Update 1
As a best practice use https://my.vmware.com/web/vmware/details?downloadGroup=SSL-TOOL-101&productId=285
Download tool & extract it in C: (for eg C:\SSLAutomationTool1.0.1)
Generate the CSR file
Under the folder find the file 'ssl-environment.bat' > Right Click > Edit
Go to "The following parameters will be used to generate a CSR."
Fill in the below fields
################
set gen_cert_server_fqdn=51-SSL-TOOL.rock.com
set gen_cert_server_ip=10.125.224.125
set gen_cert_server_short_name=51-SSL-TOOL
set gen_cert_country=IN
set gen_cert_state=KAR
set gen_cert_locality_name=BLR
set gen_cert_organization_name=VMware
################
leave 'gen_cert_organizational_unit_name' blank
Save the file
Open CMD in administrator mode
Browse to C:\SSLAutomationTool1.0.1
Type - ssl-updater.bat
Select option 2 to generate certificates requests
I will be focusing on the main vCenter components
Give the details if not already taken by the tool
If taken then just press enter like in screenshots below
All the CSR files are in C:\SSLAutomationTool1.0.1\requests\
Create a folder 'c:\certs'
Copy/paste contents from C:\SSLAutomationTool1.0.1\requests\ to c:\certs\
rename the folders to easy names
Copy c:\certs folder to desktop of Microsoft CA machine.
Generate the required certificates
Note: Make sure the Microsoft CA is configured to create vCenter server certificate - http://sslvc101.blogspot.in/p/blog-page.html
Login to http://localhost/certsrv
Note: Use IE (recommended) as other browsers behave differently & generates CER file which then again need to be renamed to CRT file.
Click the 'Request a certificate' link.
Click 'advanced certificate request'.
Click the Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file link.
Open the certificate request in a plain text editor and paste the text from the Begin to the End request into the Saved Request box:
Note: Do not copy the actual -----BEGIN CERTIFICATE REQUEST----- to -----END CERTIFICATE REQUEST-----. Only copy the text in between these lines. You may see = (equal) signs near the Begin and End lines (for example, ==-----END). In this case, you must copy the = (equal) signs.
Select the Certificate Template as 'VMware SSL' template.
Click Submit to submit the request.
Click Base 64 encoded on the Certificate issued screen.
Click the Download Certificate link.
Select 'Save As' > rui.crt in the appropriate c:\certs\<service> folder.
Do for all vCenter components
Generate Root64.cer
Login to http://localhost/certsrv
Click 'Download a CA certificate, certificate chain or CRL.'
Click the Base 64 option.
Click the Download CA Certificate chain link.
Save the certificate chain as cachain.p7b in the c:\certs folder.
Double-click the cachain.p7b file and navigate to C:\certs\cachain.p7b > Certificates.
Right-click the certificate listed and click All Actions > Export.
Click Next.
Select Base-64 encoded X.509 (.CER), then click Next.
Save the export to C:\certs\Root64.cer and click Next.
Copy/merge the 'certs' folder to VC machine & put it in C drive.
Confirm that the vCenter machine has a folder c:\certs with vCenter components folder with three files each (rui.crt, rui.csr & rui.key) & Root64.crt
Creating PEM file
Create PEM file for each service by going into each folder from command prompt
copy /B rui.crt + C:\certs\root64.cer chain.pem
Note: Run Below command if there is Subordinate CA in certification path of cert
copy /B rui.crt + C:\certs\root64-2.cer + C:\certs\root64-1.cer chain.pem
Edit the SSL automation tool configuration file
In the folder C:\SSLAutomationTool1.0.1..., edit the ssl-environment.bat as follows:
set sso_cert_chain=C:\certs\sso\chain.pem
set sso_private_key=C:\certs\sso\rui.key
set sso_node_type=single
set sso_admin_is_behind_lb=
set sso_lb_certificate= set sso_lb_hostname=
set is_cert_chain=C:\certs\inventory\chain.pem
set is_private_key_new=C:\certs\inventory\rui.key
set vc_cert_chain=C:\certs\vCenter\chain.pem
set vc_private_key=C:\certs\vCenter\rui.key
set ngc_cert_chain=C:\certs\WebClient\chain.pem
set ngc_private_key=C:\certs\WebClient\rui.key
set logbrowser_cert_chain=C:\certs\LogBrowser\chain.pem
set logbrowser_private_key=C:\certs\LogBrowser\rui.key
set vco_cert_chain=C:\certs\Orchestrator\chain.pem
set vco_private_key=C:\certs\Orchestrator\rui.key
set vum_cert_chain=C:\certs\UpdateManager\chain.pem
set vum_private_key=C:\certs\UpdateManager\rui.key
set sso_admin_user=admin@system-domain
set vc_username=rock\administrator
set last_error=
set ROLLBACK_BACKUP_FOLDER=
set LOGS_FOLDER=
Update certificates & trust
Open CMD in administrator mode
Browse to C:\SSLAutomationTool1.0.1...
Type - ssl-updater.bat
Select 1 for 'Plan your steps to update SSL certificates'
Select the services you wish to update
Copy the steps in a note pad & proceed
General Info:
SSL files which will be used in the process:
- .CRT - The actual certificate
- .CSR - Certificate Signing Request, this is required to generate the actual certificate .CRT
- .PEM - Privacy Enhanced mail - container for certificate, chain, key etc
- .KEY - This is a PEM formatted file containing just the private-key of a specific certificate
There are seven separate components in vCenter Server 5.1 that utilize certificates to encrypt communication
- SSO
- Inventory Service
- vCenter Server
- Web Client
- Log Browser
- Orchestrator
- Update Manager
Here is what we are gonna do:
- Download the SSL Automation tool
- Generate the CSR file
- Install & Configure Microsoft Certification Authority
- Generates the required certificates
- Generating PEM files
- Edit the SSL automation tool configuration file
- Update certificates & trust
Download the SSL Automation tool
Version 1.0 of the tool is supported with vSphere 5.1
Version 1.0.1 of the tool is supported with vSphere 5.1 Update 1
As a best practice use https://my.vmware.com/web/vmware/details?downloadGroup=SSL-TOOL-101&productId=285
Download tool & extract it in C: (for eg C:\SSLAutomationTool1.0.1)
Generate the CSR file
Under the folder find the file 'ssl-environment.bat' > Right Click > Edit
Go to "The following parameters will be used to generate a CSR."
Fill in the below fields
################
set gen_cert_server_fqdn=51-SSL-TOOL.rock.com
set gen_cert_server_ip=10.125.224.125
set gen_cert_server_short_name=51-SSL-TOOL
set gen_cert_country=IN
set gen_cert_state=KAR
set gen_cert_locality_name=BLR
set gen_cert_organization_name=VMware
################
leave 'gen_cert_organizational_unit_name' blank
Save the file
Open CMD in administrator mode
Browse to C:\SSLAutomationTool1.0.1
Type - ssl-updater.bat
Select option 2 to generate certificates requests
I will be focusing on the main vCenter components
- SSO
- Inventory Service
- vCenter Server
- vSphere Web Client
Give the details if not already taken by the tool
If taken then just press enter like in screenshots below
All the CSR files are in C:\SSLAutomationTool1.0.1\requests\
Create a folder 'c:\certs'
Copy/paste contents from C:\SSLAutomationTool1.0.1\requests\ to c:\certs\
rename the folders to easy names
Copy c:\certs folder to desktop of Microsoft CA machine.
Generate the required certificates
Note: Make sure the Microsoft CA is configured to create vCenter server certificate - http://sslvc101.blogspot.in/p/blog-page.html
Login to http://localhost/certsrv
Note: Use IE (recommended) as other browsers behave differently & generates CER file which then again need to be renamed to CRT file.
Click the 'Request a certificate' link.
Click 'advanced certificate request'.
Click the Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file link.
Open the certificate request in a plain text editor and paste the text from the Begin to the End request into the Saved Request box:
Note: Do not copy the actual -----BEGIN CERTIFICATE REQUEST----- to -----END CERTIFICATE REQUEST-----. Only copy the text in between these lines. You may see = (equal) signs near the Begin and End lines (for example, ==-----END). In this case, you must copy the = (equal) signs.
Select the Certificate Template as 'VMware SSL' template.
Click Submit to submit the request.
Click Base 64 encoded on the Certificate issued screen.
Click the Download Certificate link.
Select 'Save As' > rui.crt in the appropriate c:\certs\<service> folder.
Do for all vCenter components
Generate Root64.cer
Login to http://localhost/certsrv
Click 'Download a CA certificate, certificate chain or CRL.'
Click the Base 64 option.
Click the Download CA Certificate chain link.
Save the certificate chain as cachain.p7b in the c:\certs folder.
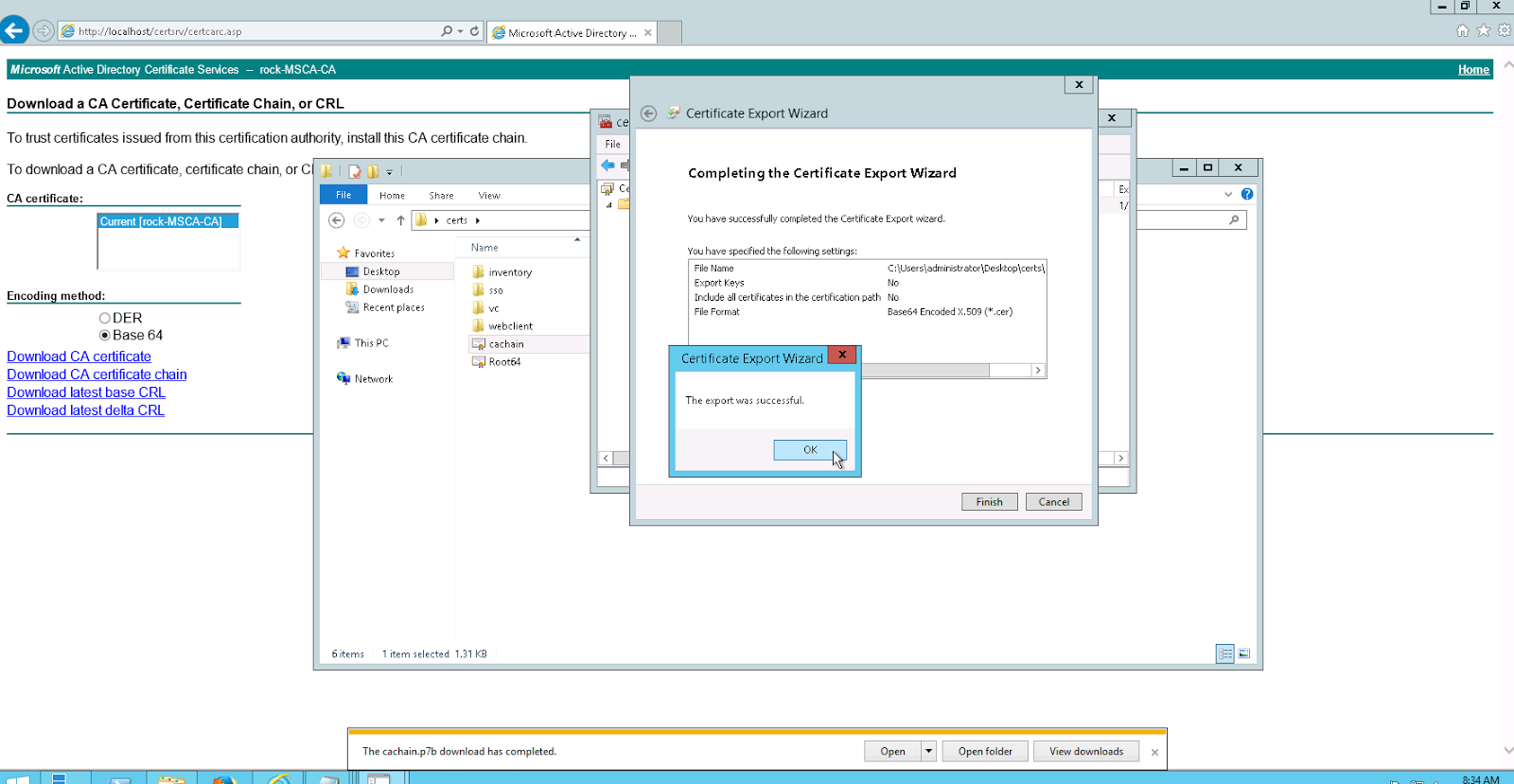
Double-click the cachain.p7b file and navigate to C:\certs\cachain.p7b > Certificates.
Right-click the certificate listed and click All Actions > Export.
Click Next.
Select Base-64 encoded X.509 (.CER), then click Next.
Save the export to C:\certs\Root64.cer and click Next.
Copy/merge the 'certs' folder to VC machine & put it in C drive.
Confirm that the vCenter machine has a folder c:\certs with vCenter components folder with three files each (rui.crt, rui.csr & rui.key) & Root64.crt
Creating PEM file
Create PEM file for each service by going into each folder from command prompt
copy /B rui.crt + C:\certs\root64.cer chain.pem
Note: Run Below command if there is Subordinate CA in certification path of cert
copy /B rui.crt + C:\certs\root64-2.cer + C:\certs\root64-1.cer chain.pem
Edit the SSL automation tool configuration file
In the folder C:\SSLAutomationTool1.0.1..., edit the ssl-environment.bat as follows:
set sso_cert_chain=C:\certs\sso\chain.pem
set sso_private_key=C:\certs\sso\rui.key
set sso_node_type=single
set sso_admin_is_behind_lb=
set sso_lb_certificate= set sso_lb_hostname=
set is_cert_chain=C:\certs\inventory\chain.pem
set is_private_key_new=C:\certs\inventory\rui.key
set vc_cert_chain=C:\certs\vCenter\chain.pem
set vc_private_key=C:\certs\vCenter\rui.key
set ngc_cert_chain=C:\certs\WebClient\chain.pem
set ngc_private_key=C:\certs\WebClient\rui.key
set logbrowser_cert_chain=C:\certs\LogBrowser\chain.pem
set logbrowser_private_key=C:\certs\LogBrowser\rui.key
set vco_cert_chain=C:\certs\Orchestrator\chain.pem
set vco_private_key=C:\certs\Orchestrator\rui.key
set vum_cert_chain=C:\certs\UpdateManager\chain.pem
set vum_private_key=C:\certs\UpdateManager\rui.key
set sso_admin_user=admin@system-domain
set vc_username=rock\administrator
set last_error=
set ROLLBACK_BACKUP_FOLDER=
set LOGS_FOLDER=
Update certificates & trust
Open CMD in administrator mode
Browse to C:\SSLAutomationTool1.0.1...
Type - ssl-updater.bat
Select 1 for 'Plan your steps to update SSL certificates'
Select the services you wish to update
Copy the steps in a note pad & proceed








































































































Thanks for sharing this article about SSL,
ReplyDelete"secure ssl"
I have found your article really nice and helpful,
ReplyDeleteAfordable website Christchurch
Thanks for this really nice and helpful article,.
ReplyDeletewhois lookup
This is something really amazing and helpful,
ReplyDeleteweb hosting services in pakistan
Wow.. That's so informative. Thanks a ton... I would also recommend people to visit a site, mysslonline
ReplyDelete